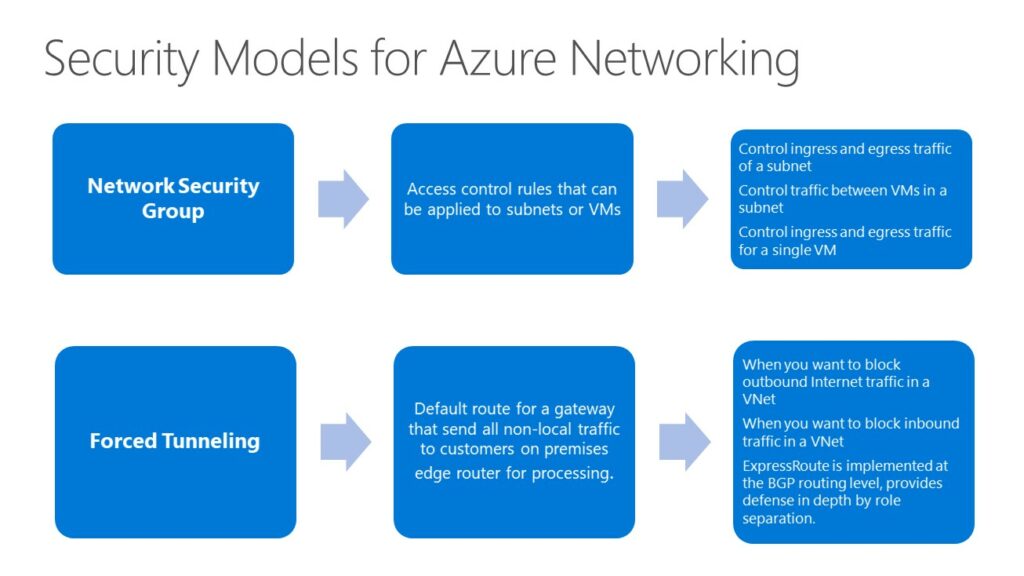
Network Security Groups (NSG) :
- Enables network segmentation & DMZ scenarios
- Access Control Lists & Network traffic rules as security group
- Security groups associated with Virtual machines, Network Interfaces, or virtual machine subnets (not GW subnet)
- Rules define a 5-tuple
- Rules are separated into Inbound and Outbound rules
- Rules applied in order of priority
- Network traffic rules updated independent of Virtual machines
- Controlled access to and from Internet
Network Security Group Models : At the subnet level and at the VM level.
- Subnet Level NSGs: An NSG rule is applied to a subnet is logically more like a firewall rule that is applied at the switch and affects inbound and outbound traffic on every port in the switch. Any VM connected to the switch port would be affected by the NSG rule applied to the subnet.
- VM/NIC Level NSGs: Apply NSGs at the VM or NIC of a virtual machine. This allows greater flexibility in how traffic is filtered.
Forced Tunneling
- “Force” or redirect customer Internet-bound traffic to an on premises site via default route
- VPN – done per subnet
- ExpressRoute – at BGP level
- Can override with more specific routes via UDR
 NSG and forced tunneling
NSG and forced tunneling