Azure has built-in functionality for discovering and classifying sensitive data, surfacing and mitigating potential database vulnerabilities, and detecting anomalous activities that could indicate a threat to your database.
Those powerful features are part of the Advanced Data Security (ADS) package for advanced SQL security. Specifically, Advanced Threat Protection for Azure SQL Database and SQL Data Warehouse detects anomalous activities indicating unusual and potentially harmful attempts to access or exploit databases:
- Vulnerability to SQL Injection
- Potential SQL injection
- Access from unusual location
- Access from unusual data center
- Access from unfamiliar principal
- Access from potentially harmful application
- Brute force SQL Credentials
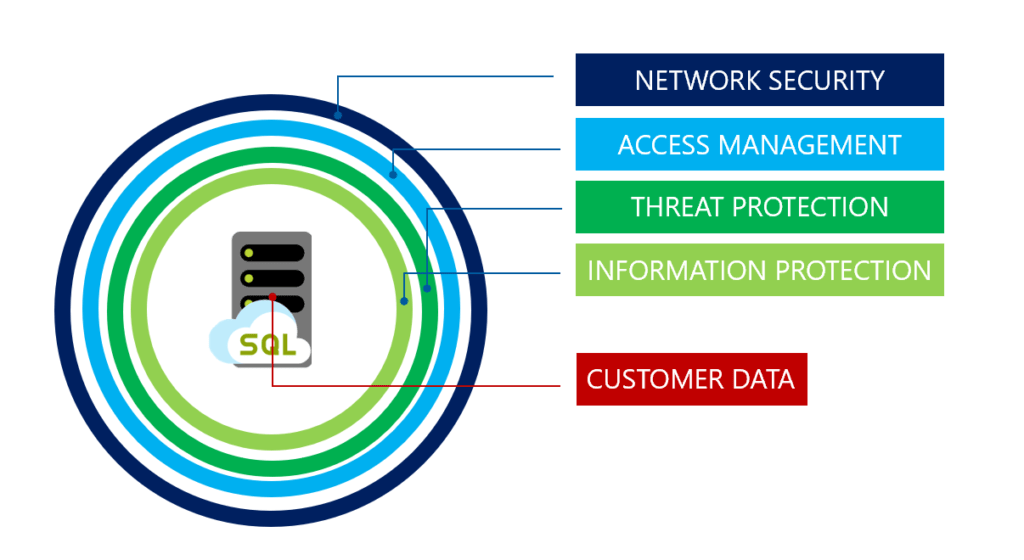 Advanced Threat Protection for Azure SQL Database
Advanced Threat Protection for Azure SQL Database
The cost of ADS is aligned with Azure Security Center standard tier pricing per node, where a node is the entire SQL Database server or managed instance. You are thus paying only once for protecting all databases on the database server or managed instance with ADS.
Another feature of Azure Security, part of the above mentioned ADS, is SQL Vulnerability Assessment.
Vulnerability Assessment is a scanning service built into the Azure SQL Database service. The service employs a knowledge base of rules that flag security vulnerabilities and highlight deviations from best practices, such as misconfigurations, excessive permissions, and unprotected sensitive data. The rules are based on Microsoft’s best practices and focus on the security issues that present the biggest risks to your database and its valuable data. We recommend using regularly this service, as it can provide valuable insight into your database security posture.