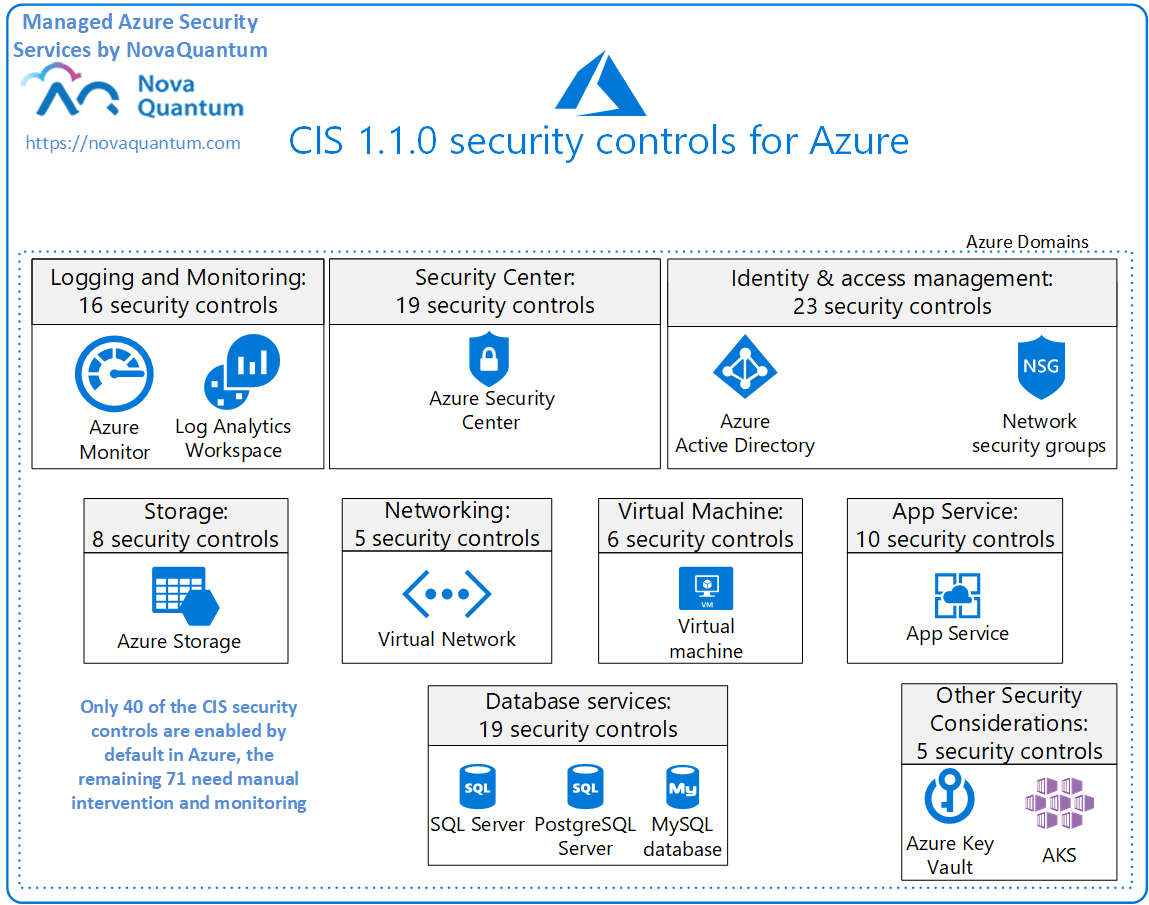
CIS Microsoft Azure Foundations Benchmark security controls are listed below (please note that although this is the complete list of all the controls specified by the CIS standard, only 48 of them have been enabled for automatic auditing in Azure and very few of them have any automated remediation available, most of them require manual steps and need a regular review to make sure any changes done to existing resources and the new resources added to the environment still comply with them- our Managed Azure Security Service solves all those problems!):
| Domain | Nr | Security Control Name |
| Identity and Access Management | 1.1 | Ensure that multi-factor authentication is enabled for all privileged users |
| 1.2 | Ensure that multi-factor authentication is enabled for all non-privileged users | |
| 1.3 | Ensure that there are no guest users | |
| 1.4 | Ensure that ‘Allow users to remember multi-factor authentication on devices they trust’ is ‘Disabled’ | |
| 1.5 | Ensure that ‘Number of methods required to reset’ is set to ‘2’ | |
| 1.6 | Ensure that ‘Number of days before users are asked to re-confirm their authentication information’ is not set to “0” | |
| 1.7 | Ensure that ‘Notify users on password resets?’ is set to ‘Yes’ | |
| 1.8 | Ensure that ‘Notify all admins when other admins reset their password?’ is set to ‘Yes’ | |
| 1.9 | Ensure that ‘Users can consent to apps accessing company data on their behalf’ is set to ‘No’ | |
| 1.1 | Ensure that ‘Users can add gallery apps to their Access Panel’ is set to ‘No’ | |
| 1.11 | Ensure that ‘Users can register applications’ is set to ‘No’ | |
| 1.12 | Ensure that ‘Guest user permissions are limited’ is set to ‘Yes’ | |
| 1.13 | Ensure that ‘Members can invite’ is set to ‘No’ | |
| 1.14 | Ensure that ‘Guests can invite’ is set to ‘No’ | |
| 1.15 | Ensure that ‘Restrict access to Azure AD administration portal’ is set to ‘Yes’ | |
| 1.16 | Ensure that ‘Self-service group management enabled’ is set to ‘No’ | |
| 1.17 | Ensure that ‘Users can create security groups’ is set to ‘No’ | |
| 1.18 | Ensure that ‘Users who can manage security groups’ is set to ‘None’ | |
| 1.19 | Ensure that ‘Users can create Office 365 groups’ is set to ‘No’ | |
| 1.20 | Ensure that ‘Users who can manage Office 365 groups’ is set to ‘None’ | |
| 1.21 | Ensure that ‘Enable “All Users” group’ is set to ‘Yes’ | |
| 1.22 | Ensure that ‘Require Multi-Factor Auth to join devices’ is set to ‘Yes’ | |
| 1.23 | Ensure that no custom subscription owner roles are created |
| Domain | Nr | Security Control Name |
| Security Center | 2.1 | Ensure that standard pricing tier is selected |
| 2.2 | Ensure that ‘Automatic provisioning of monitoring agent’ is set to ‘On’ | |
| 2.3 | Ensure ASC Default policy setting “Monitor System Updates” is not “Disabled” | |
| 2.4 | Ensure ASC Default policy setting “Monitor OS Vulnerabilities” is not “Disabled” | |
| 2.5 | Ensure ASC Default policy setting “Monitor Endpoint Protection” is not “Disabled” | |
| 2.6 | Ensure ASC Default policy setting “Monitor Disk Encryption” is not “Disabled” | |
| 2.7 | Ensure ASC Default policy setting “Monitor Network Security Groups” is not “Disabled” | |
| 2.8 | Ensure ASC Default policy setting “Monitor Web Application Firewall” is not “Disabled” | |
| 2.9 | Ensure ASC Default policy setting “Enable Next Generation Firewall(NGFW) Monitoring” is not “Disabled” | |
| 2.10 | Ensure ASC Default policy setting “Monitor Vulnerability Assessment” is not “Disabled” | |
| 2.11 | Ensure ASC Default policy setting “Monitor Storage Blob Encryption” is not “Disabled” | |
| 2.12 | Ensure ASC Default policy setting “Monitor JIT Network Access” is not “Disabled” | |
| 2.13 | Ensure ASC Default policy setting “Monitor Adaptive Application Whitelisting” is not “Disabled” | |
| 2.14 | Ensure ASC Default policy setting “Monitor SQL Auditing” is not “Disabled” | |
| 2.15 | Ensure ASC Default policy setting “Monitor SQL Encryption” is not “Disabled” | |
| 2.16 | Ensure that ‘Security contact emails’ is set | |
| 2.17 | Ensure that security contact ‘Phone number’ is set | |
| 2.18 | Ensure that ‘Send email notification for high severity alerts’ is set to ‘On’ | |
| 2.19 | Ensure that ‘Send email also to subscription owners’ is set to ‘On’ |
| Domain | Nr | Security Control Name |
| Storage Accounts | 3.1 | Ensure that ‘Secure transfer required’ is set to ‘Enabled’ |
| 3.2 | Ensure that storage account access keys are periodically regenerated | |
| 3.3 | Ensure Storage logging is enabled for Queue service for read, write, and delete requests | |
| 3.4 | Ensure that shared access signature tokens expire within an hour | |
| 3.5 | Ensure that shared access signature tokens are allowed only over https | |
| 3.6 | Ensure that ‘Public access level’ is set to Private for blob containers | |
| 3.7 | Ensure default network access rule for Storage Accounts is set to deny | |
| 3.8 | Ensure ‘Trusted Microsoft Services’ is enabled for Storage Account access |
| Domain | Nr | Security Control Name |
| Database Services | 4.1 | Ensure that ‘Auditing’ is set to ‘On’ |
| 4.2 | Ensure that ‘AuditActionGroups’ in ‘auditing’ policy for a SQL server is set properly | |
| 4.3 | Ensure that ‘Auditing’ Retention is ‘greater than 90 days’ | |
| 4.4 | Ensure that ‘Advanced Data Security’ on a SQL server is set to ‘On’ | |
| 4.5 | Ensure that ‘Threat Detection types’ is set to ‘All’ | |
| 4.6 | Ensure that ‘Send alerts to’ is set | |
| 4.7 | Ensure that ‘Email service and co-administrators’ is ‘Enabled’ | |
| 4.8 | Ensure that Azure Active Directory Admin is configured | |
| 4.9 | Ensure that ‘Data encryption’ is set to ‘On’ on a SQL Database | |
| 4.1 | Ensure SQL server’s TDE protector is encrypted with BYOK (Use your own key) | |
| 4.11 | Ensure ‘Enforce SSL connection’ is set to ‘ENABLED’ for MySQL Database Server | |
| 4.12 | Ensure server parameter ‘log_checkpoints’ is set to ‘ON’ for PostgreSQL Database Server | |
| 4.13 | Ensure ‘Enforce SSL connection’ is set to ‘ENABLED’ for PostgreSQL Database Server | |
| 4.14 | Ensure server parameter ‘log_connections’ is set to ‘ON’ for PostgreSQL Database Server | |
| 4.15 | Ensure server parameter ‘log_disconnections’ is set to ‘ON’ for PostgreSQL Database Server | |
| 4.16 | Ensure server parameter ‘log_duration’ is set to ‘ON’ for PostgreSQL Database Server | |
| 4.17 | Ensure server parameter ‘connection_throttling’ is set to ‘ON’ for PostgreSQL Database Server | |
| 4.18 | Ensure server parameter ‘log_retention_days’ is greater than 3 days for PostgreSQL Database Server | |
| 4.19 | Ensure that Azure Active Directory Admin is configured |
| Domain | Nr | Security Control Name |
| Configuring Log Profile | 5.1.1 | Ensure that a Log Profile exists |
| 5.1.2 | Ensure that Activity Log Retention is set 365 days or greater | |
| 5.1.3 | Ensure audit profile captures all the activities | |
| 5.1.4 | Ensure the log profile captures activity logs for all regions including global | |
| 5.1.5 | Ensure the storage container storing the activity logs is not publicly accessible | |
| 5.1.6 | Ensure the storage account containing the container with activity logs is encrypted with BYOK (Use Your Own Key) | |
| 5.1.7 | Ensure that logging for Azure KeyVault is ‘Enabled’ | |
| Monitoring using Activity Log Alerts | 5.2.1 | Ensure that Activity Log Alert exists for Create Policy Assignment |
| 5.2.2 | Ensure that Activity Log Alert exists for Create or Update Network Security Group | |
| 5.2.3 | Ensure that Activity Log Alert exists for Delete Network Security Group | |
| 5.2.4 | Ensure that Activity Log Alert exists for Create or Update Network Security Group Rule | |
| 5.2.5 | Ensure that activity log alert exists for the Delete Network Security Group Rule | |
| 5.2.6 | Ensure that Activity Log Alert exists for Create or Update Security Solution | |
| 5.2.7 | Ensure that Activity Log Alert exists for Delete Security Solution | |
| 5.2.8 | Ensure that Activity Log Alert exists for Create or Update or Delete SQL Server Firewall Rule | |
| 5.2.9 | Ensure that Activity Log Alert exists for Update Security Policy |
| Domain | Nr | Security Control Name |
| Networking | 6.1 | Ensure that RDP access is restricted from the internet |
| 6.2 | Ensure that SSH access is restricted from the internet | |
| 6.3 | Ensure no SQL Databases allow ingress 0.0.0.0/0 (ANY IP) | |
| 6.4 | Ensure that Network Security Group Flow Log retention period is ‘greater than 90 days’ | |
| 6.5 | Ensure that Network Watcher is ‘Enabled’ | |
| Virtual Machines | 7.1 | Ensure that ‘OS disk’ are encrypted |
| 7.2 | Ensure that ‘Data disks’ are encrypted | |
| 7.3 | Ensure that ‘Unattached disks’ are encrypted | |
| 7.4 | Ensure that only approved extensions are installed | |
| 7.5 | Ensure that the latest OS Patches for all Virtual Machines are applied | |
| 7.6 | Ensure that the endpoint protection for all Virtual Machines is installed | |
| Other Security Considerations | 8.1 | Ensure that the expiration date is set on all keys |
| 8.2 | Ensure that the expiration date is set on all Secrets | |
| 8.3 | Ensure that Resource Locks are set for mission critical Azure resources | |
| 8.4 | Ensure the key vault is recoverable | |
| 8.5 | Enable role-based access control (RBAC) within Azure Kubernetes Services | |
| AppService | 9.1 | Ensure App Service Authentication is set on Azure App Service |
| 9.2 | Ensure web app redirects all HTTP traffic to HTTPS in Azure App Service | |
| 9.3 | Ensure web app is using the latest version of TLS encryption | |
| 9.4 | Ensure the web app has ‘Client Certificates (Incoming client certificates)’ set to ‘On’ | |
| 9.5 | Ensure that Register with Azure Active Directory is enabled on App Service | |
| 9.6 | Ensure that ‘.Net Framework’ version is the latest, if used as a part of the web app | |
| 9.7 | Ensure that ‘PHP version’ is the latest, if used to run the web app | |
| 9.8 | Ensure that ‘Python version’ is the latest, if used to run the web app | |
| 9.9 | Ensure that ‘Java version’ is the latest, if used to run the web app | |
| 9.10 | Ensure that ‘HTTP Version’ is the latest, if used to run the web app |