This is Part#7 of our series of articles about best security practices that you can apply to an Azure environment. Please note that all the articles have been compiled from various official Microsoft sources.
Internet EDGE Strategy: For your core services segment you can choose between native controls and 3rd party capabilities for internet traffic filtering.
What : Choose whether to use Native Azure Controls or 3rd party Network Virtual Appliances (NVAs) for internet edge security (North-South)
Why : Legacy workloads require network protection from internet sources and there are advantages to using either 1st or 3rd party controls to provide this.
How : Select a strategy using the comparison information below
| AZURE NATIVE CONTROLS Basic capabilities with simple integration & management | 3rd Party Capabilities Advanced security capabilities from existing vendors |
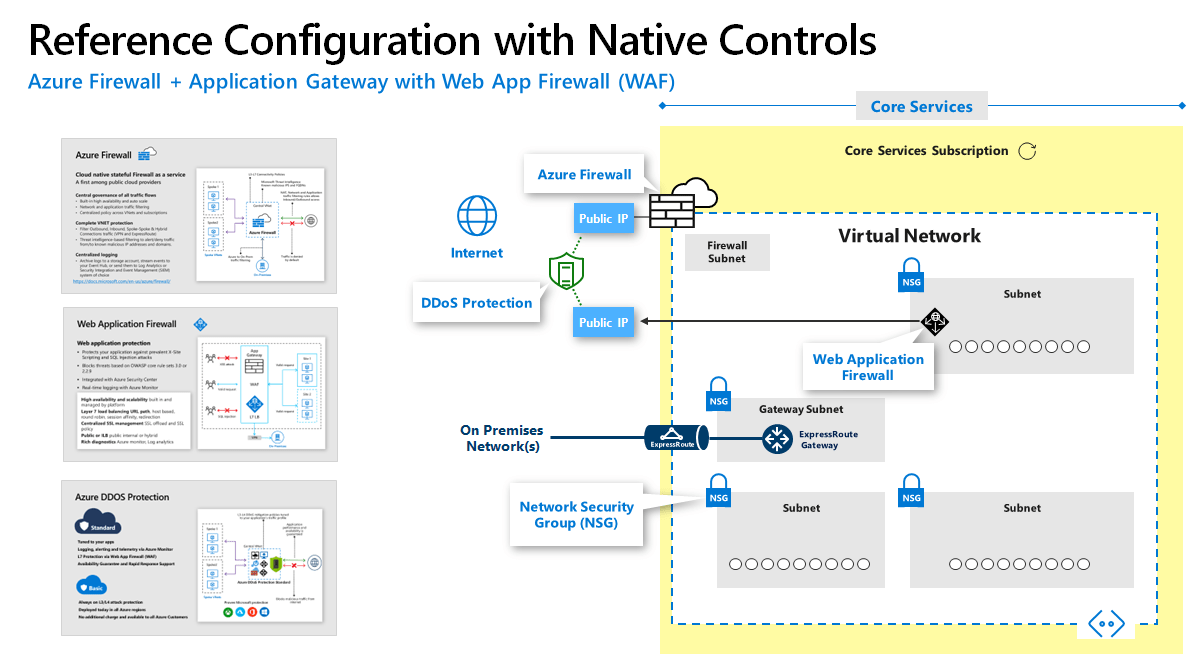
| Azure Firewall + Web App Firewall (in Application Gateway) These offer basic security that is good enough for some scenarios with a fully stateful firewall as a service, built-in high availability, unrestricted cloud scalability, FQDN filtering, support for OWASP core rule sets, and simple setup and configuration | Next Generation Firewall (NGFW) and other 3rd party offerings Network virtual appliances in the Azure Marketplace include familiar security tools that provide enhanced network security capabilities Configuration is more complex, but allows you to leverage existing capabilities, and skillets |
Reference Azure Firewall Configuration with Native Controls