This is Part#4 of our series of articles about best security practices that you can apply to an Azure environment. Please note that all the articles have been compiled from various official Microsoft sources.
Security Operations – Azure Alerts
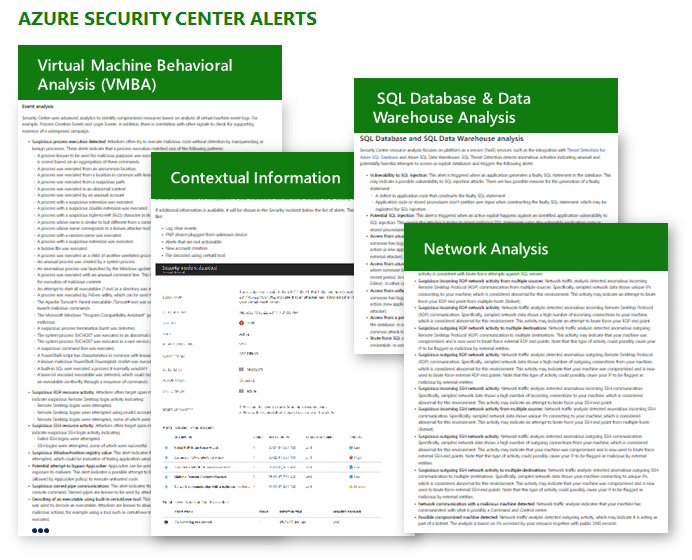
What : Enable Azure Security Center security Alerts
Why : Azure Security Center provides actionable detections for common attack methods which can save your team significant effort on query development.
These alerts are focused on high true positive rate by leveraging Microsoft’s extensive threat intelligence, advanced machine learning, industry leading Endpoint Detection & Response (EDR) (MITRE report), and other approaches.
How : Enable Azure Security Center (We recommend Standard Tier to gain full control over all the security options)
Security Operations – Centralized Visibility
Use Azure Security Center and Azure Sentinel to create your own Security Dashboard.
Azure Security Center is focused on protection and governance of Azure Workloads by assessing risk to them, reducing attack surface, and generating alerts on potential threats using advanced threat detection technologies. The roles who use ASC will typically include security engineers and GRC Professionals that report risk to the CISO.
Azure Sentinel is focused on monitoring All Environments by SOC analysts. Azure Sentinel allows for monitoring alerts and security related events from any source (Microsoft security solutions, 3rd party, custom rules). Azure Sentinel is built for security analysts and SOC managers to make their work easier and more effective. Azure Sentinel is designed to simplify the application of advanced technologies like Machine Learning, User and Entity Behavior Analytics (UEBA), to the variety of data-sets you monitor and is complemented by other Microsoft Threat Protection solutions that provide specialized investigation of hosts, email, identity attacks, and more.
Azure Security Operations – Centralized Visibility