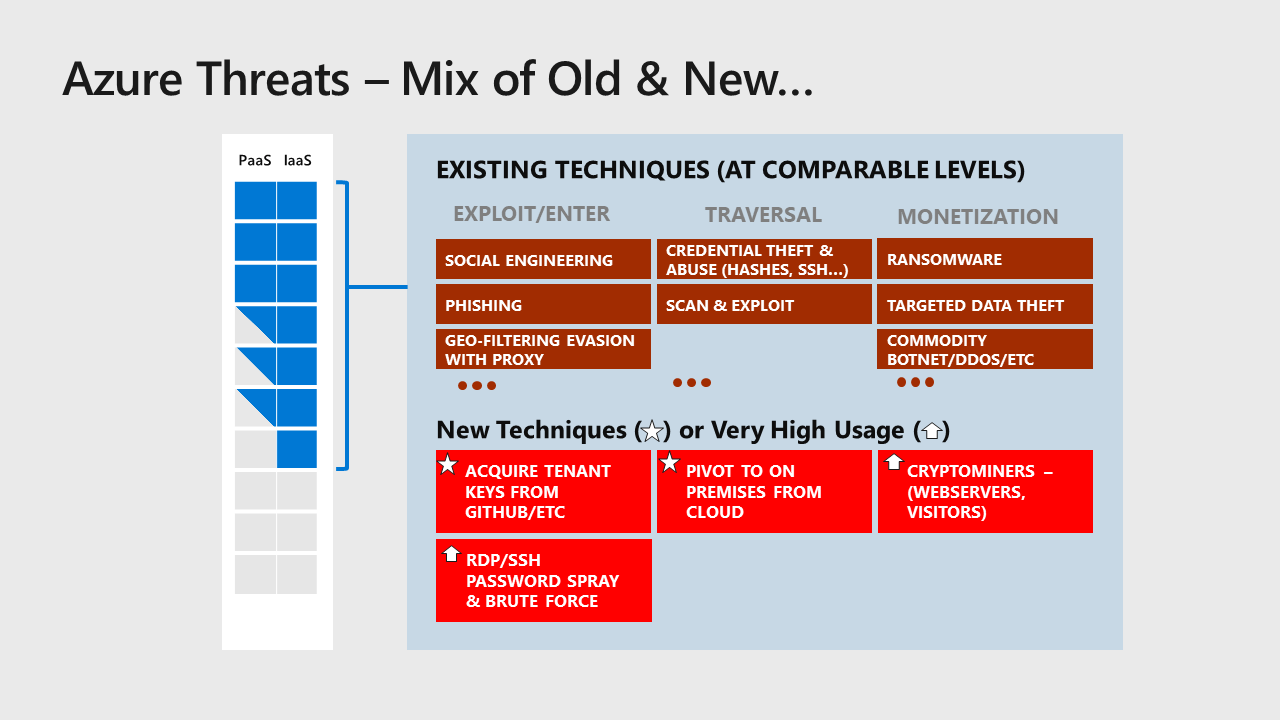
Many attack vectors are seen at about the same rate as on-premises including social engineering, phishing and ransomware. Microsoft has observed some differences from traditional on premises attacks including:
- Theft and Abuse of Keys – Many cloud access can accept keys for authentication (storage, services, etc.). Many developers are unfamiliar with security best practices for key management and embed these keys directly into their code. This source code is then frequently posted publicly to services like GitHub where attackers can find them and use them to illicitly access those resources.
- RDP/SSH Password Spray and Brute Force – The technique of scanning for open RDP/SSH ports and trying common passwords has been around for some time. This attack requires extra attention in Azure because the public IP address ranges of cloud providers are scanned with a very high intensity and there is a higher chance of misconfiguring network security because of unfamiliarity with the controls
- Pivot to on premises from cloud – An attack vector that didn’t exist before the cloud is that attackers who have compromised a resource can pivot to Azure from on-premises and vice-versa. Because cloud infrastructure is effectively just another datacenter in your enterprise estate, you need to ensure the security is equal to or greater than your on premises posture.
- Cryptominers – While the rise of cryptominer attacks is likely not due to the cloud itself, these attacks have become prevalent recently. This typically takes the form of compromising an internet facing web server and using that server to mine cryptocurrencies or embedding code into the website to perform the mining on browsers/clients that visit the site.